Ransomware has been an emerging threat for the last years. In May this year, a specific Ransomware called WannaCry brought news back onto this topic. While working on a paper on ransomware, I did some research on how ransomware attacks can be prevented - or how malware can be hidden from Antivirus software.
Ransomware typically encrypts user data to extort a certain amount of money (mostly demanded as Bitcoin transfer). There are other types of ransomware that only lock the user’s desktop to extort money. But as this type usually does no permanent damage, I will leave it aside in this post.
Backups
The most effective strategy against ransomware is having a current backup of your data in a physically separated location. If the backup is kept on the same system, the ransomware might encrypt it as well. Unfortunately, many users won’t create backups.
Antivirus Software
A commonly used recommendation to PC users is to install an antivirus software. But does antivirus software really protect you from ransomware attacks? Let a little experiment show how effective antivirus software really is against ransomware:
Setting
Luckily, we have a copy of the hidden tear ransomware available on GitHub. Hidden tear is written in C#. The compiled binary of this source code has a 53/60 VirusTotal detection rate1.
In this experiment, I modified the original source code in certain ways in order to hide it from antivirus software. I did not change anything functional, though. The changed binaries were uploaded to virustotal.com to test their detection rates.
| Change | Description |
|---|---|
| Project name | The string hidden tear is removed from the whole project. This includes file name, AssemblyInfo and string constants. |
| Symbols | The C# compiler keeps all class, method and variable names as string literals in the resulting binaries. Therefore, all symbols are replaced with a random string. |
| Obfuscation | I let Crypto Obfuscator for .Net run over the compiled binaries2. It’s usually there to prevent reverse engineering of your app, but hey, isn’t that sort of what antivirus software does? |
Results
The following table shows the aggregated results of the VirusTotal tests:
| Nr. | Change | Obfuscator | Detected | Scanners total | Rate | Link |
|---|---|---|---|---|---|---|
| A | None | None | 53 | 60 | 88,33% | Link |
| B | Project name | None | 34 | 60 | 56,67% | Link |
| C | Symbols | None | 31 | 61 | 50,82% | Link |
| D | Project name + symbols | None | 18 | 61 | 29,51% | Link |
| E | None | Default | 18 | 60 | 30,00% | Link |
| F | Project name | Default | 16 | 60 | 26,67% | Link |
| G | Symbols | Default | 19 | 60 | 31,67% | Link |
| H | Project name + symbols | Default | 10 | 60 | 16,67% | Link |
| I | None | Full | 19 | 59 | 32,20% | Link |
| J | Project name | Full | 18 | 61 | 29,51% | Link |
| K | Symbols | Full | 19 | 61 | 31,15% | Link |
| L | Project name + symbols | Full | 10 | 61 | 16,39% | Link |
I’m leaving out the detailed table of which antivirus detects which version of hidden tear. But as you can see, simply stripping out the name of the malicious executable (Version B) tempts as much as 19 more antivirus systems to go “ah, carry on, sorry I disturbed you”. And as I clearly want to state here, even a 99.99% overall detection rate of a certain malware or a 99.99% detection rate of a certain antivirus over all kinds of malware isn’t enough. If that 0.01% ransomware hits you, if you don’t have a backup, your data is lost.
To confirm that the results are valid and not based on some strange configuration at VirusTotal, I installed an antivirus myself and let my modified version of hidden tear do its work (in a VM, of course!). With a small shell script I created 1000 files with random names and content.
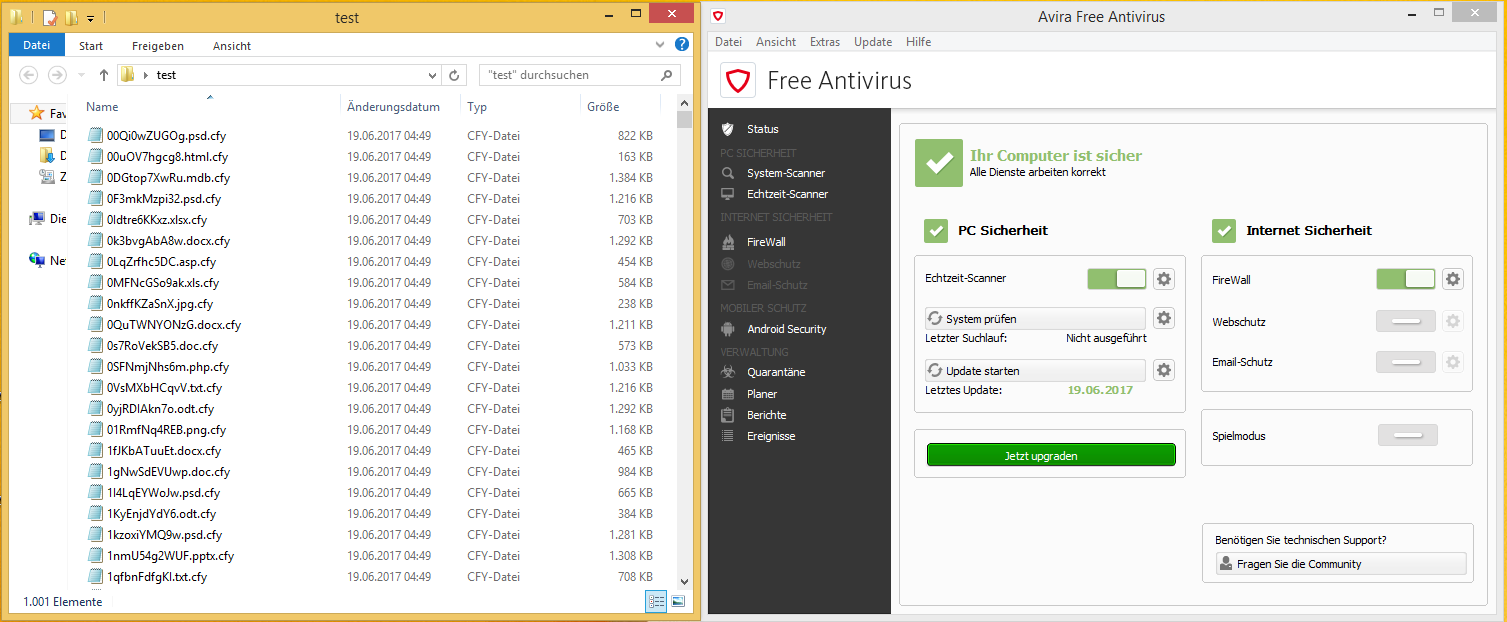
As you can see in the above picture, my version of hidden tear encrypted all 1000 files while Avira still claims the system is “safe”.
CryptoDrop
In 2016, Nolen Scaife, Henry Carter, Patrick Traynor and Kevin R.B. Butler published a paper that could finally help to fight back ransomware attacks. Their tool CryptoDrop doesn’t examine the malicious executable itself like antivirus software does. CryptoDrop looks at the actions executables perform on files. They identified three main factors for a working ransomware on the system:
- A changing file type
- A change of file contents with no similarity
- A significant increase of entropy
Because strong encryption is designed to leave no hint about the original plain text and to hold only a minimum amount of entropy, the above factors are quite a strong hint that ransomware is encrypting some files. However, a bunch of other metrics is used to be sure: Mass deletion of files or reading an unusual big variety of different file types can also be a signal for unwanted behavior.
The authors claim to be able to identify and kill a ransomware process with a median of 10 files encrypted. Unfortunately, there isn’t a downloadable sample of CryptoDrop yet to test it on my above scenario.
Conclusions
Ransomware is a big threat to our data. Fighting it is hard, but antivirus software is no relief. The changes to the existing ransomware made in this experiment are so minimal, it’s really embarrassing they’re sufficient to trick antivirus software.